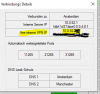
When cascading VPns, the VPN Manager currently still doesn't display the 3 random opened ports. For sure there exists a formula to derive these 3 ports from the exit server's internal VPN IP, but manually using it each time is really boring and inconvenient
For Linux users, the FAQ offers a batch code to automate the calculation:
But nothing for poor Windows users.
So, were it possible to translate the prev(c)ious code in a windows compliant one???
(The best would be that the Vpn Manager displays these ports, even when using a vpn cascade, though)
For Linux users, the FAQ offers a batch code to automate the calculation:
Code:
#!/bin/bash
[[ "$#" -eq 1 ]] || exit 1
IPv4_ADDR=${1}
IFS='.' read -ra ADDR <<< "$IPv4_ADDR"
function d2b() {
printf "%08d" $(echo "obase=2;$1"|bc)
}
port_bin="$(d2b ${ADDR[2]})$(d2b ${ADDR[3]})"
port_dec=$(printf "%04d" $(echo "ibase=2;${port_bin:4}"|bc))
for i in 1 2 3; do
echo "$i$port_dec"
doneSo, were it possible to translate the prev(c)ious code in a windows compliant one???
(The best would be that the Vpn Manager displays these ports, even when using a vpn cascade, though)