Hallo zusammen,
leider habe ich Probleme damit meinen Traffic via Opevnvpn durch einen Linksys WRT1900ACSv2 zu routen. Der OpenVPN Tunnel verbindet sich aber mein Netzwerkadapter tun0 bekommt keine IP.
Sehr ihr noch ein Problem?
Ich vermute, dass es Probleme mit meinem Unitymedia Anschluss und DS-Lite sind. OpenVPN versucht sich wohl nur via IPv4 zu verbinden. Wenn ich als Protokoll upd6 oder tcp6 wähle funktioniert es leider auch nicht, dann kann er Erfurt als Server nicht auflösen.
Habt ihr noch eine Idee, vor allem in Bezug auf ipv6 DSLITE?
Vielen Dank!

OpenVPN connection Log
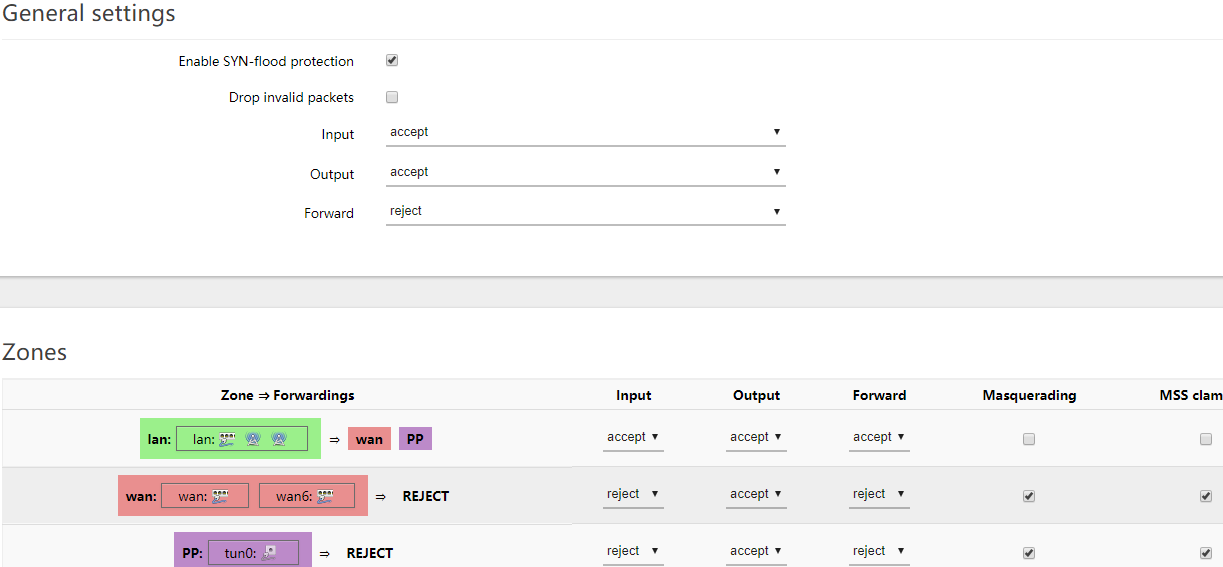
Firewall settings:
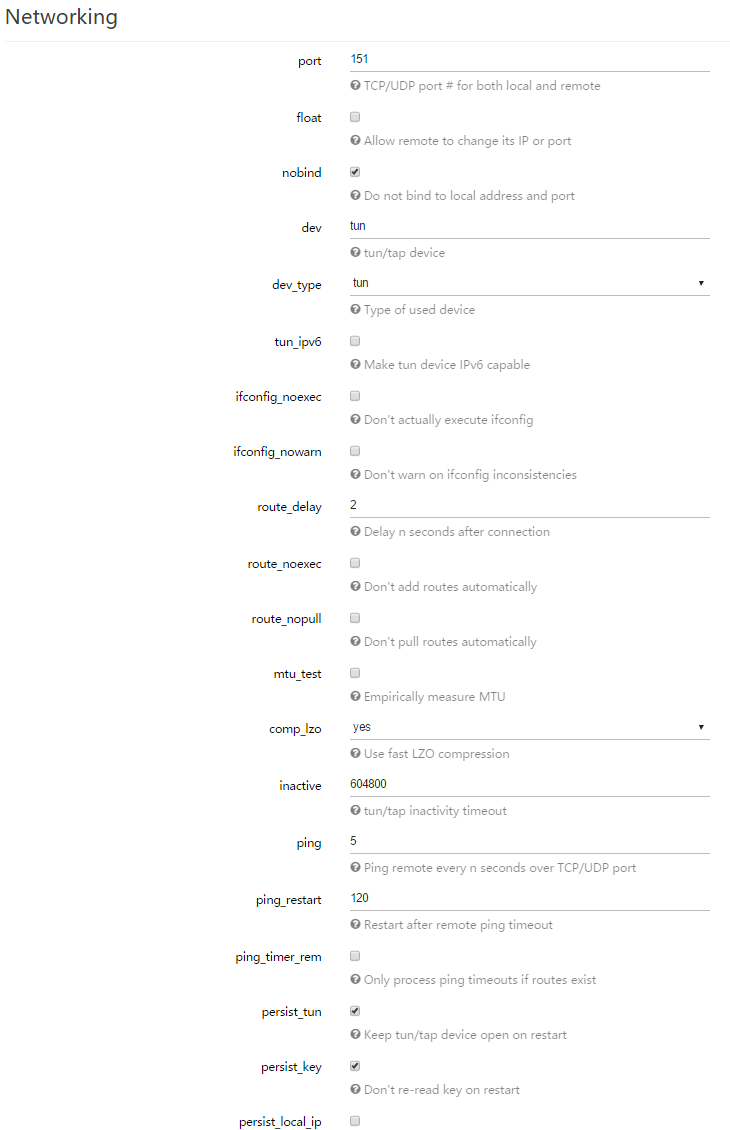
OpenVPN Config:
leider habe ich Probleme damit meinen Traffic via Opevnvpn durch einen Linksys WRT1900ACSv2 zu routen. Der OpenVPN Tunnel verbindet sich aber mein Netzwerkadapter tun0 bekommt keine IP.
Sehr ihr noch ein Problem?
Ich vermute, dass es Probleme mit meinem Unitymedia Anschluss und DS-Lite sind. OpenVPN versucht sich wohl nur via IPv4 zu verbinden. Wenn ich als Protokoll upd6 oder tcp6 wähle funktioniert es leider auch nicht, dann kann er Erfurt als Server nicht auflösen.
Habt ihr noch eine Idee, vor allem in Bezug auf ipv6 DSLITE?
Vielen Dank!



OpenVPN connection Log
Sun Mar 11 20:21:39 2018 daemon.warn openvpn(sample_client)[16066]: Note: option tun-ipv6 is ignored because modern operating systems do not need special IPv6 tun handling anymore.
Sun Mar 11 20:21:39 2018 daemon.warn openvpn(sample_client)[16066]: WARNING: Ignoring option 'dh' in tls-client mode, please only include this in your server configuration
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: OpenVPN 2.4.4 arm-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: library versions: OpenSSL 1.0.2n 7 Dec 2017, LZO 2.10
Sun Mar 11 20:21:39 2018 daemon.warn openvpn(sample_client)[16066]: WARNING: --ns-cert-type is DEPRECATED. Use --remote-cert-tls instead.
Sun Mar 11 20:21:39 2018 daemon.warn openvpn(sample_client)[16066]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: Initializing OpenSSL support for engine 'dynamic'
Sun Mar 11 20:21:39 2018 daemon.warn openvpn(sample_client)[16066]: WARNING: Failed to stat CRL file, not (re)loading CRL.
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: LZO compression initializing
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: Control Channel MTU parms [ L:1622 D:1140 EF:110 EB:0 ET:0 EL:3 ]
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1602,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 1,cipher AES-256-CBC,auth SHA512,keysize 256,tls-auth,key-method 2,tls-client'
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1602,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 0,cipher AES-256-CBC,auth SHA512,keysize 256,tls-auth,key-method 2,tls-server'
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: TCP/UDP: Preserving recently used remote address: [AF_INET]111.000.000.000:1194
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: Socket Buffers: R=[163840->163840] S=[163840->163840]
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: UDP link local: (not bound)
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: UDP link remote: [AF_INET]111.000.000.000:1194
Sun Mar 11 20:21:39 2018 daemon.notice openvpn(sample_client)[16066]: NOTE: UID/GID downgrade will be delayed because of --client, --pull, or --up-delay
Firewall settings:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config zone
option name 'PP'
option output 'ACCEPT'
option network 'tun0'
option masq '1'
option mtu_fix '1'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option dest 'PP'
option src 'lan'
OpenVPN Config:
config openvpn 'sample_client'
option client '1'
option proto 'udp'
option nobind '1'
option persist_key '1'
option persist_tun '1'
option user 'nobody'
option compress 'lzo'
option ca '/etc/luci-uploads/cbid.openvpn.sample_client.ca'
option cert '/etc/luci-uploads/cbid.openvpn.sample_client.cert'
option dev_type 'tun'
option key '/etc/luci-uploads/cbid.openvpn.sample_client.key'
option key_direction '1'
option dh '/etc/easy-rsa/keys/dh1024.pem'
option enabled '1'
option tun_ipv6 '1'
option port '1194'
list remote 'someserveraddress.com'
option persist_remote_ip '1'
option resolv_retry '60'
option mute_replay_warnings '1'
option auth 'SHA512'
option tls_auth '/etc/openvpn/tlsauth.key'
option auth_user_pass '/etc/openvpn/userpass.txt'
option route_delay '0'
option redirect_gateway 'def1'
option cipher 'AES-256-CBC'
option tls_version_min '1.0'
option tls_version_max '1.2'
option tls_cipher 'TLS-DHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-CBC-SHA256:TLS-DHE-RSA-WITH-CAMELLIA-256-CBC-SHA:TLS-DHE-RSA-WITH-AES-256-CBC-SHA:TLS-RSA-WITH-CAMELLIA-256-CBC-SHA:TLS-RSA-WITH-AES-256-CBC-SHA'
option ns_cert_type 'server'
option reneg_sec '3600'
option crl_verify '/etc/easy-rsa/keys/crl.pem'
option engine 'dynamic'
option script_security '2'
option verb '4'
option tls_timeout '2'
option tls_remote 'remote_x509_name'
option remote_cert_tls 'client'
option comp_lzo 'yes'
option remote_random '1'
option ping_restart '120'
option ping '5'
option inactive '604800'
option key_method '2'
option down '/usr/bin/ovpn-down'
option tls_client '1'
option route_gateway '192.168.1.1'
option dev 'tun0'
list push 'dhcp-option DNS 223.134.241.10’
list push 'block-outside-dns’
list push 'route 192.168.1.0 255.255.255.0'
list push 'redirect-gateway def1'
Last edited: