Well, I got it working. Here are the instructions, presented as what must be changed and added to the Perfect Privacy Setup Instructions for pfSense.
1. Go to menu VPN > OpenVPN > Clients
Edit the line for your OpenVPN Client interface.
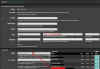
General Information
Protocol: UDP IPv4 and IPv6 on all interfaces (multihome)
Advanced Configuration
Custom options: the options given in the Perfect Privacy Setup didn't work well for me -- the interface was constantly cycling from being on to off. If the options given in the setup work for you, keep them. Otherwise, here are the options I find work well for me:
Code:
verb 5
tun-mtu 1500
fragment 1300
tun-ipv6
mssfix
#float
hand-window 120
inactive 604800
mute-replay-warnings
#ns-cert-type server
remote-cert-tls server
persist-remote-ip
#redirect-gateway def1
reneg-sec 0
resolv-retry infinite
keepalive 10 60
key-direction 1
persist-tun
persist-key
verb 4
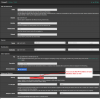
Gateway creation: Check "Both" [important -- this causes both IPv4 and IPv6 gateways to be created]
2. Go to menu Firewall > NAT > Outbound
Add a new rule
Edit Advanced Outbound NAT Entry
Interface: OpenVPN
Address Family: IPv6
Protocol: any
Source: Network address: your IPV6 LAN prefix (see notes below)
Destination: Any [unchanged]
Translation
Address: Interface Address
Misc
Description: add a description for your rule
Note: you can see the interface address on your dashboard, under Gateways
Notes:
The "Source" address is the IPv6 network prefix for your local LAN.
- I have a 64 bit prefix, so the format is xxxx:xxxx:xxxx:xxxx:: / 64 (note: two colons at end)
- Where you can find this:
- From a Windows CMD.exe window, run ipconfig /all and look at the IPv6 address for your ethernet adaptor:
My prefix (given I have a /64 subnet) is the first 4 fields of the address
- From Linux command line, run ifconfig and look for the inet6 address:
Create a firewall rule to direct IPv6 traffic to your VPN IPv6 gateway
Edit Firewall Rule
Action: Pass
Interface: LAN
Address Family: IPv6
Protocol: Any
Source
Source: LAN net
Extra Options
Description: enter a description for your rule
Advanced Options: click on Display Advanced
Advanced Options
everything at default, except for Gateway -- make sure Gateway is set to VPN WAN IPv6 gateway
After you save that rule, pfSense should start sending IPv6 traffic over your OpenVPN IPv6 interface.
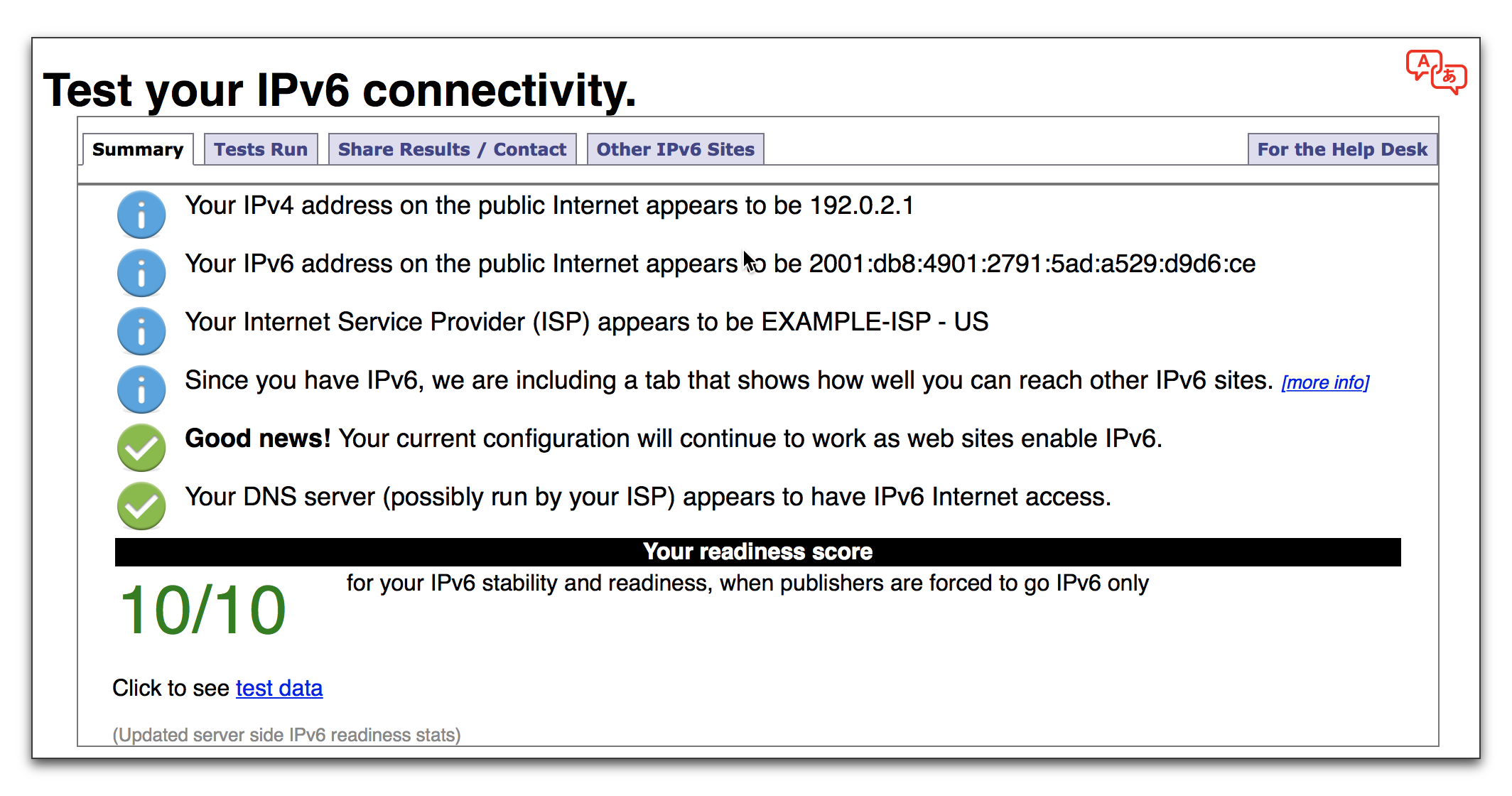
4. Test that it's working
The IP tests are run. You should see results for both the IPv4 section and the IPv6 section
Congratulations and welcome to the future.